Oracle 23c: Hybrid Read-Only Mode for Pluggable Databases
Overview: Oracle 23c database introduces a new feature to open Pluggable database in a new mode called hybrid read-only Hybrid read-only mode enables ... Read More
Learn more about why Eclipsys has been named the 2023 Best Workplaces in Technology and Ontario, Certified as a Great Place to Work in Canada and named Canada’s Top SME Employer!
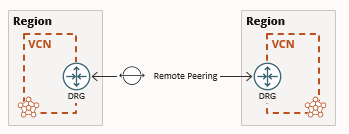
Learn more!In this blog, we will demonstrate the steps to peer two VCNs in different regions through a DRG in the same tenancy. This is called a remote VCN peering.
The peering allows the VCNs’ resources to communicate using private IP addresses without routing the traffic over the internet or through your on-premises network.
A remote peering connection (RPC) is a component you create on the DRG attached to your VCN. The RPC’s job is to act as a connection point for a remotely peered VCN. A given DRG must have a separate RPC for each remote peering it establishes for the VCN.
At a high level, the networking service components required for this scenario include:
|
|
VCN1 |
VCN2 |
|
Region |
Toronto (ca-toronto-1 |
Ashburn (us-Ashburn-1) |
|
VCN Name |
TOR-VCN |
ASH-VCN |
|
Private Subnet CIDR |
10.0.1.0/24 |
172.0.1.0/24 |
|
DRG |
TOR-DRG |
ASH-DRG |
|
RPC |
TOR-RPC |
ASH-RPC |
|
Compute Instance |
TOR-VM (10.0.1.129) |
ASH-VM (172.0.1.132) |
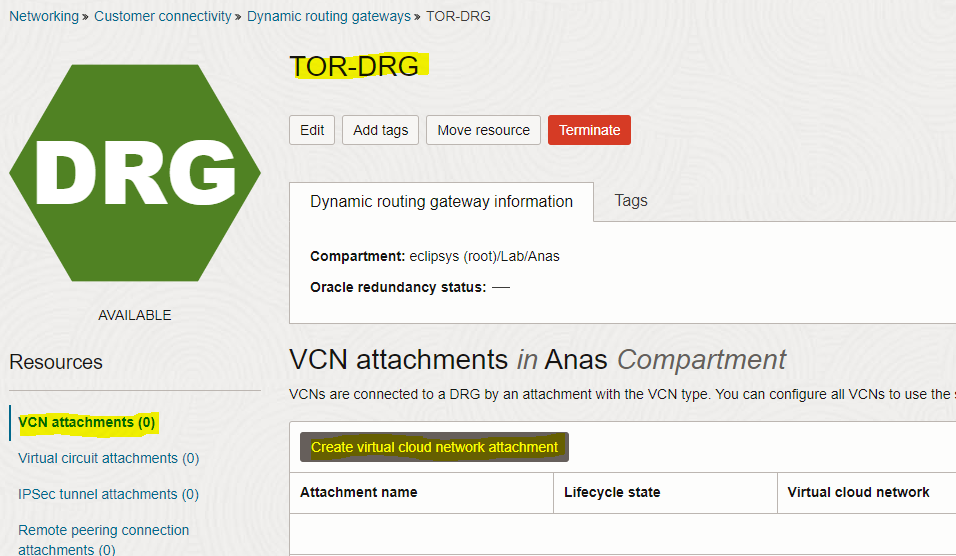
Prerequisites:
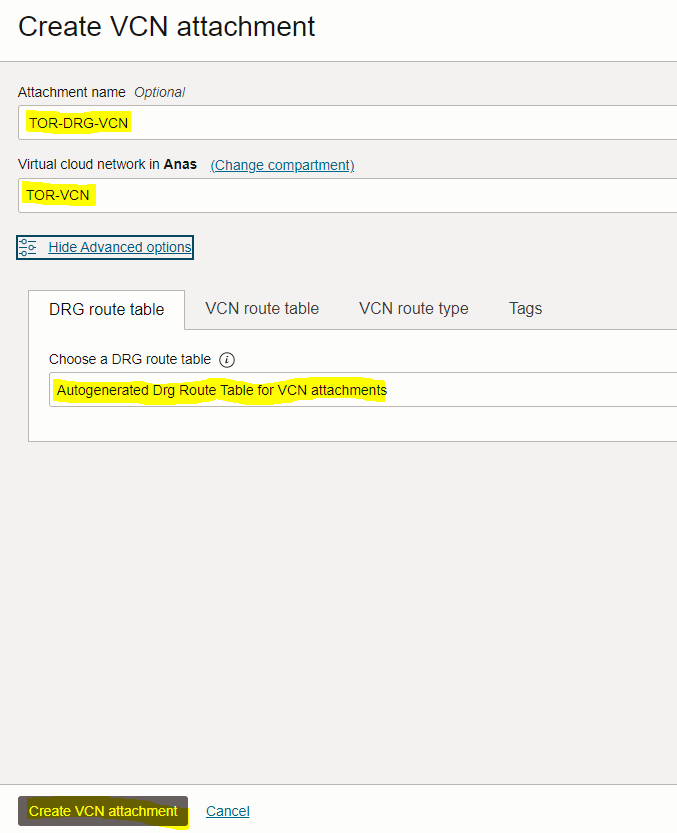
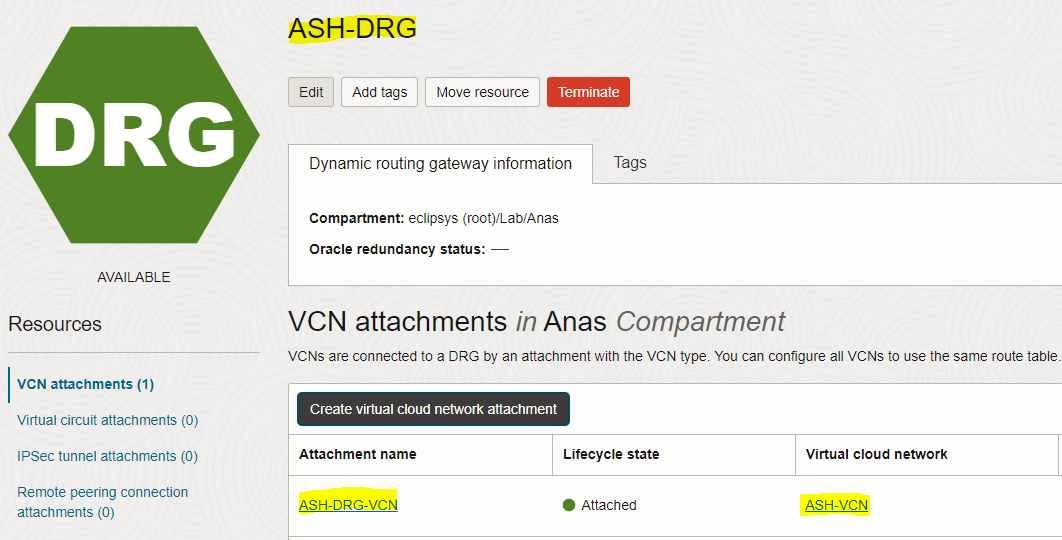
– In the “Create VCN attachment” page, enter the attachment name (TOR-DRG-VCN) and select VCN1 (TOR-VCN), then click the “Create VCN attachment” button
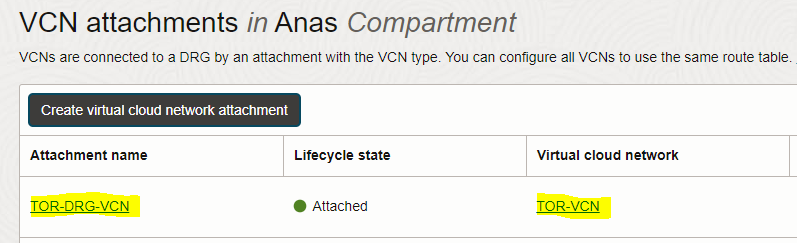
– Repeat the same steps done above to attach TOR-VCN
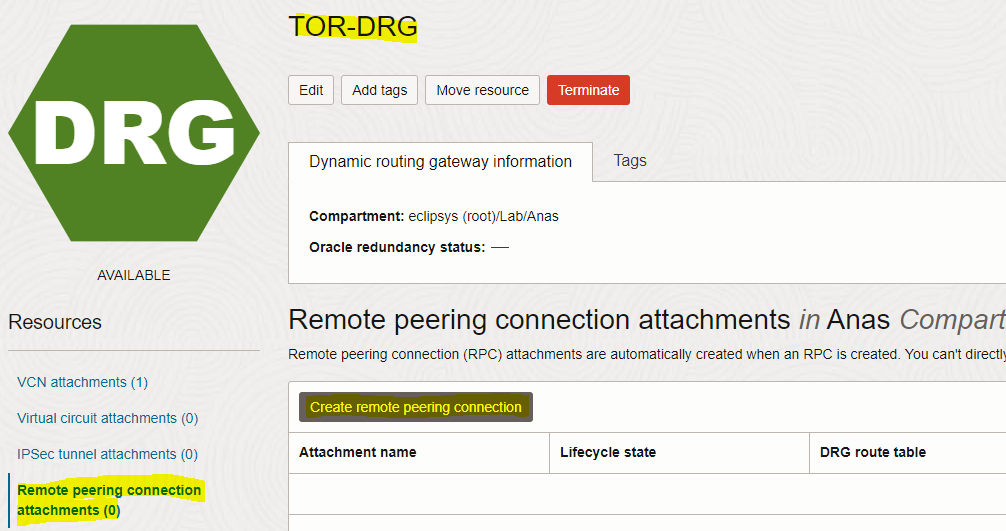
– Go to the TOR-DRG detail page and click on the “Remote peering connection attachments” tab
– Click the “Create remote peering connection” button
– In the “Create remote peering connection” page, enter the connection name and select compartment
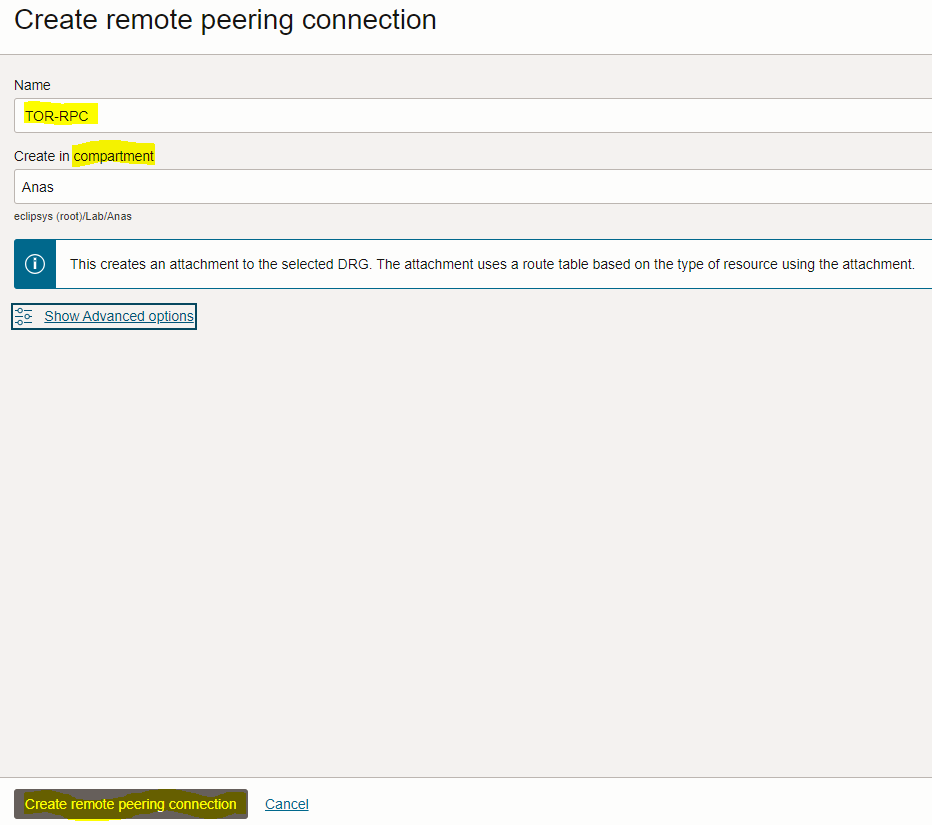
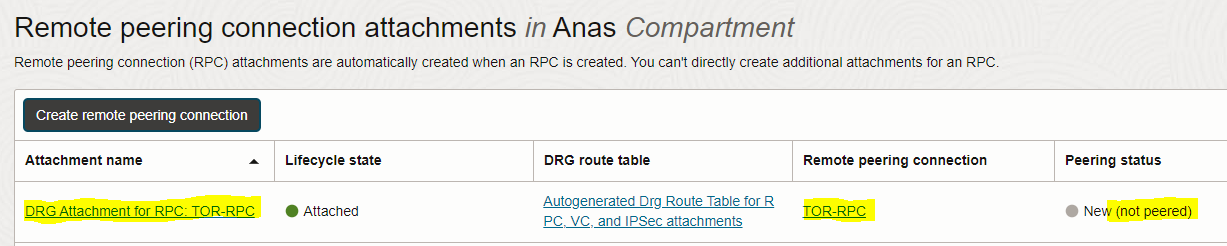
– Repeat the steps done above to create the Toronto region RPC
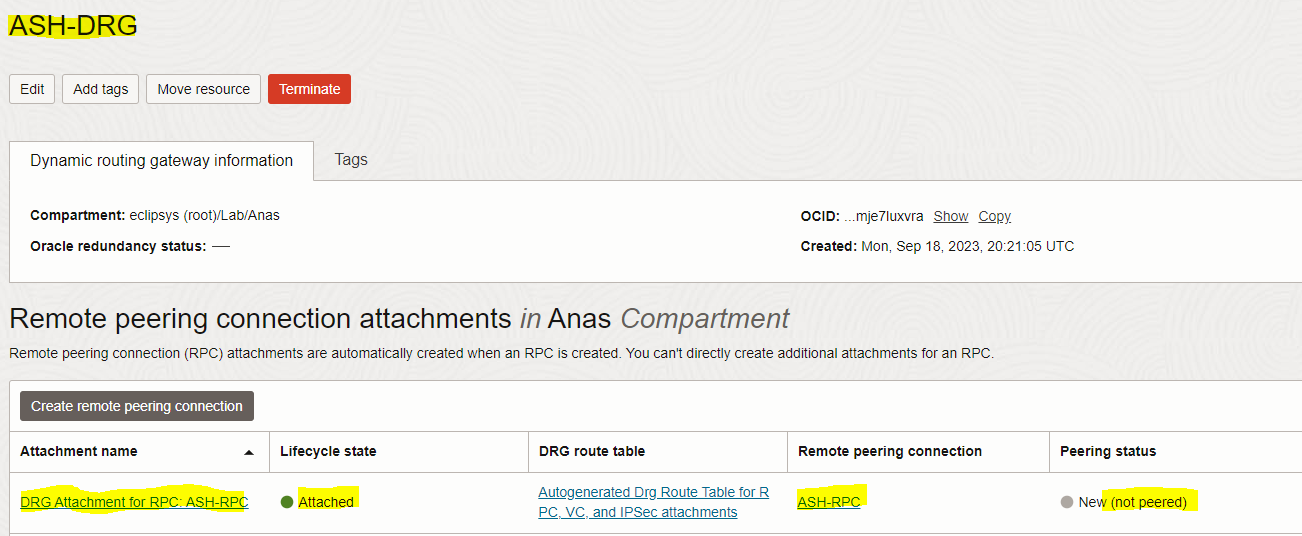
– Go to the TOR-DRG detail page and click on the “Remote peering connection attachments” tab
– View the details of TOR-RPC by clicking the name of the TOR-RPC connection in the “Remote Peering Connection” column
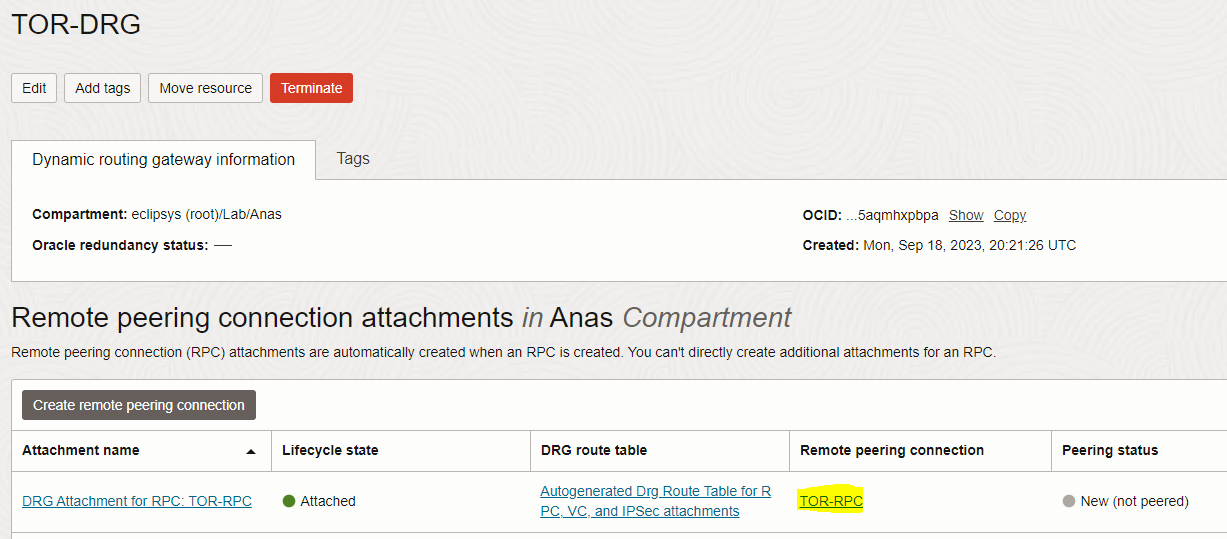
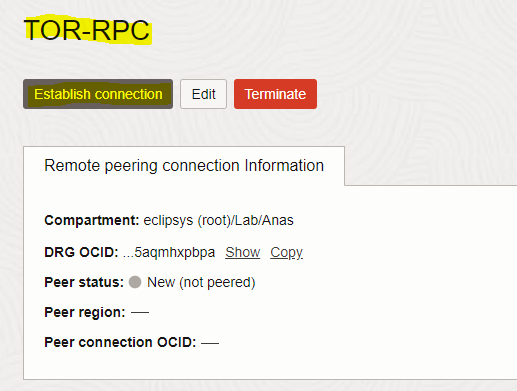
– In the connection details page, click the “Establish Connection” button, enter the connection name, and select compartment
– In the “Establish connection” page, select the “us-Ashburn-1” region and enter the OCID of Ashburn RPC (ASH-RPC) (the remote peering RPC). When The connection is established, the RPC’s state changes to PEERED
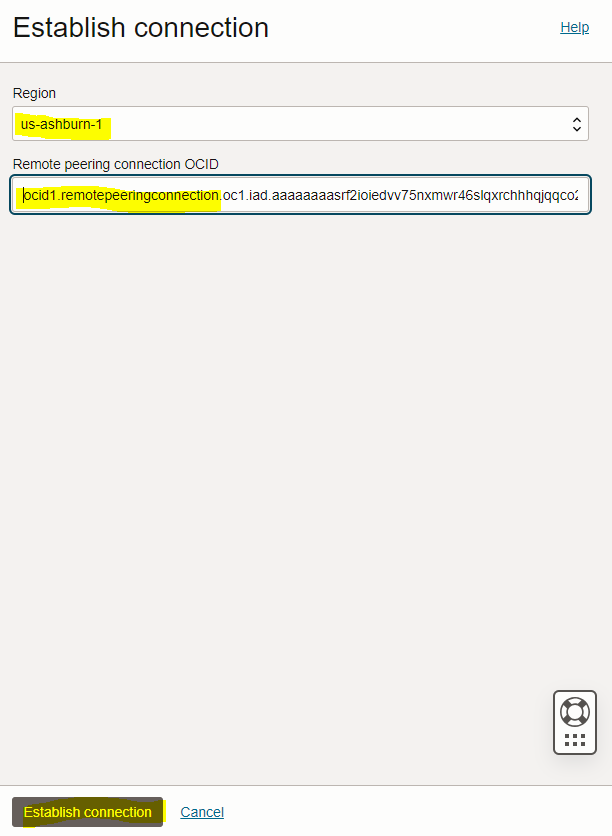
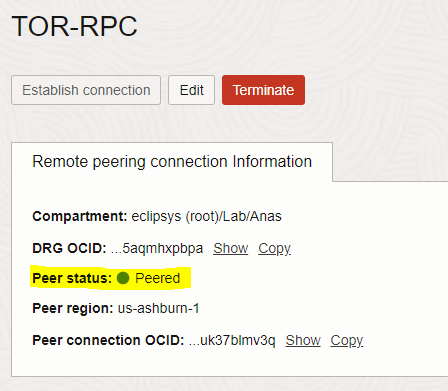
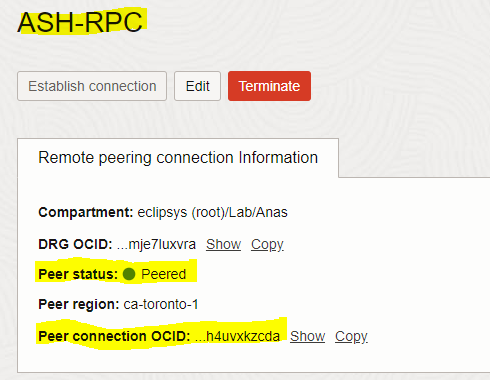
– Hence, ASH-RPC peering state changes to PEERED as well
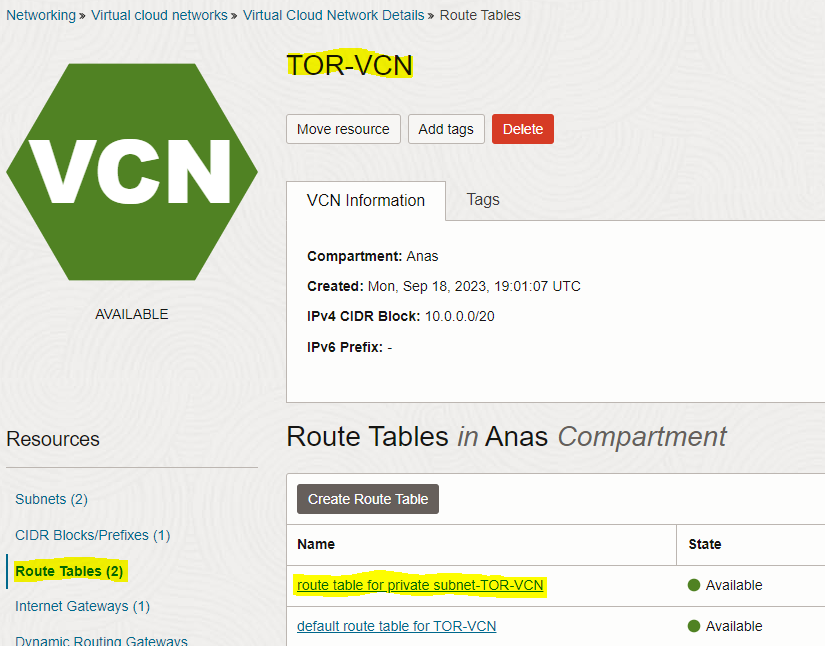
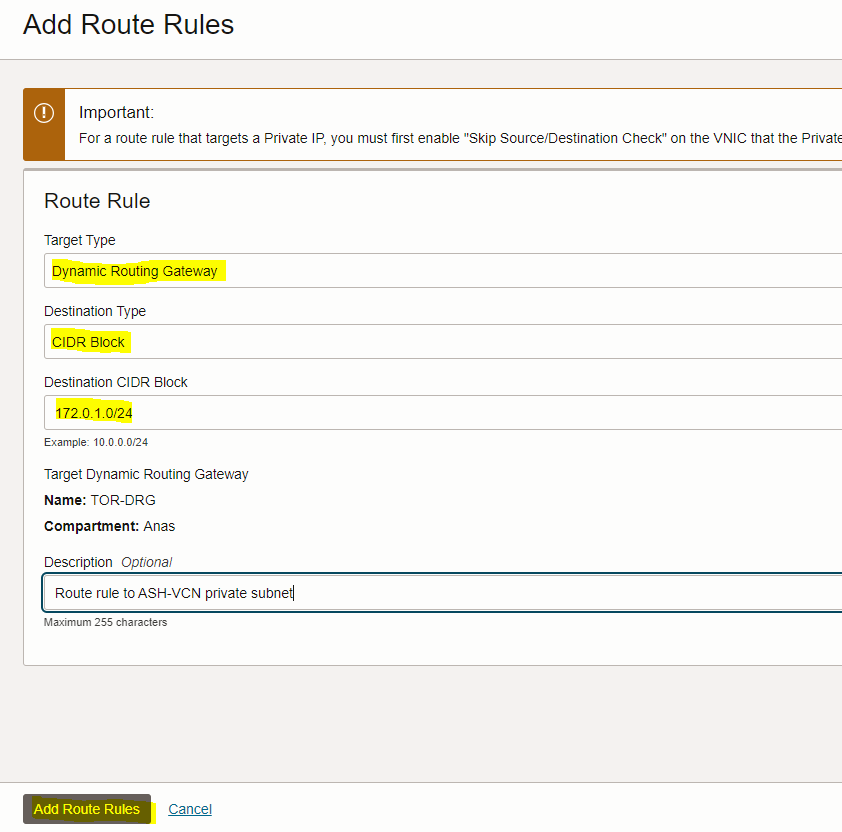
– On the route table page, click the “Add Route Rules” button and enter below route rule information below.
|
Target Type |
Destination Type |
Destination CIDR Block |
|
Dynamic Routing Gateway |
CDIR Block |
172.0.1.64/24 (VCN2-private subnet CIDR) |
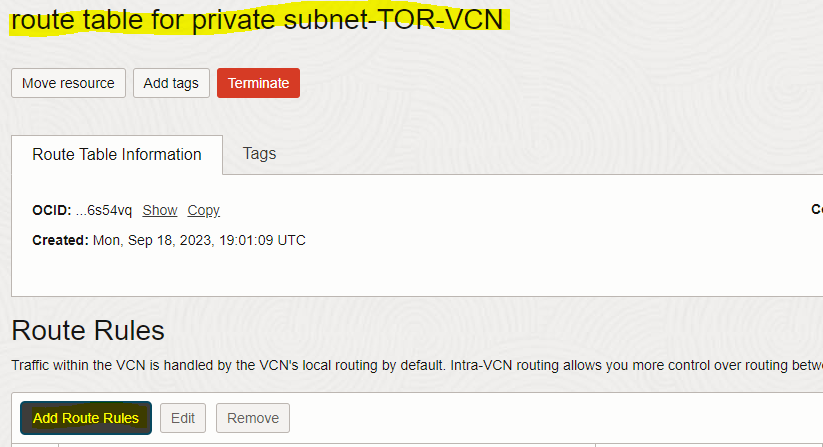
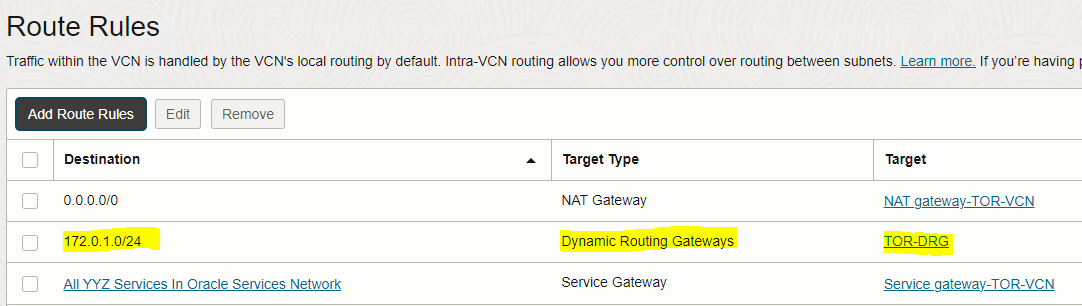
– Repeat the same steps done above to configure the route table for TOR-VCN’s private subnet
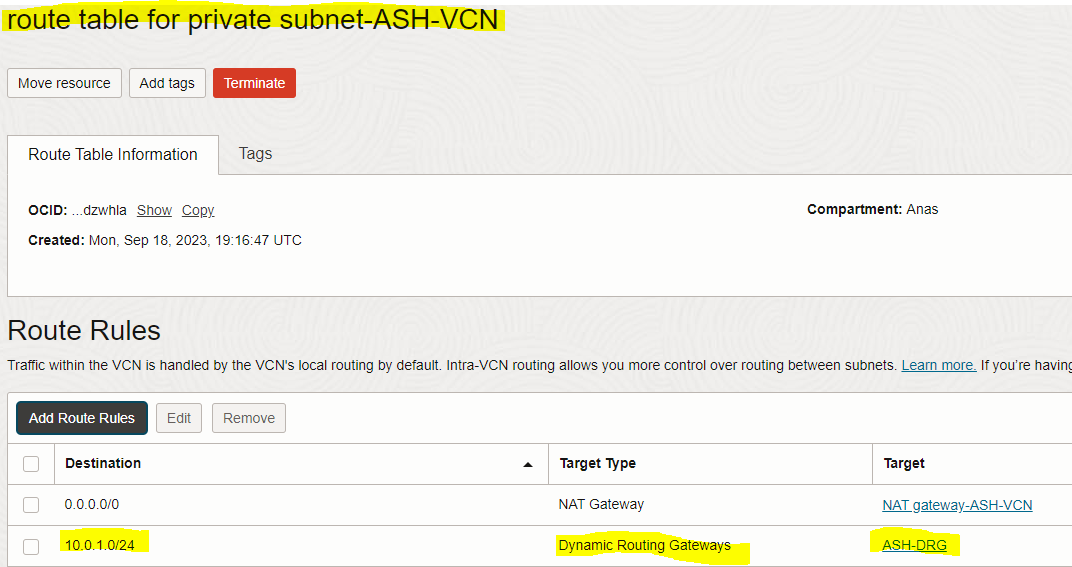
Use below rule information below.
|
Target Type |
Destination Type |
Destination CIDR Block |
|
Dynamic Routing Gateway |
CDIR Block |
10.0.1.0/24 (VCN1-private subnet CIDR) |
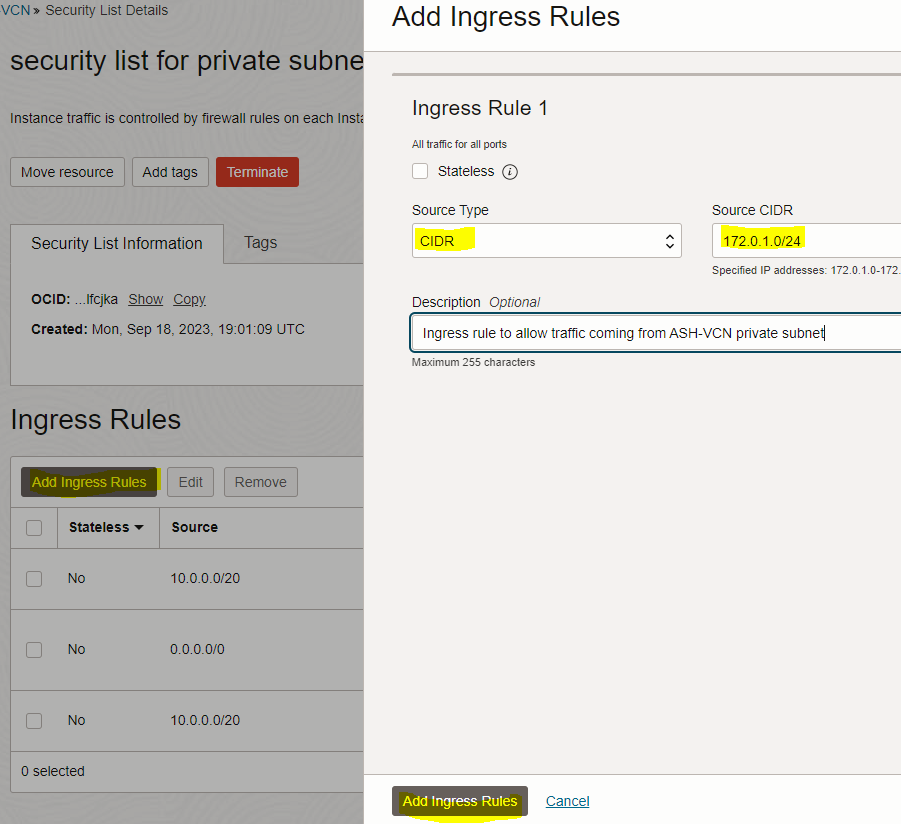
– On the Security List page, click the “Add Ingress Rules” button and enter below Ingress rule information
|
Source Type |
Source CIDR |
IP PROTOCOL |
|
CIDR |
172.0.1.0/24 (VCN2-private subnet CIDR) |
All Protocols |
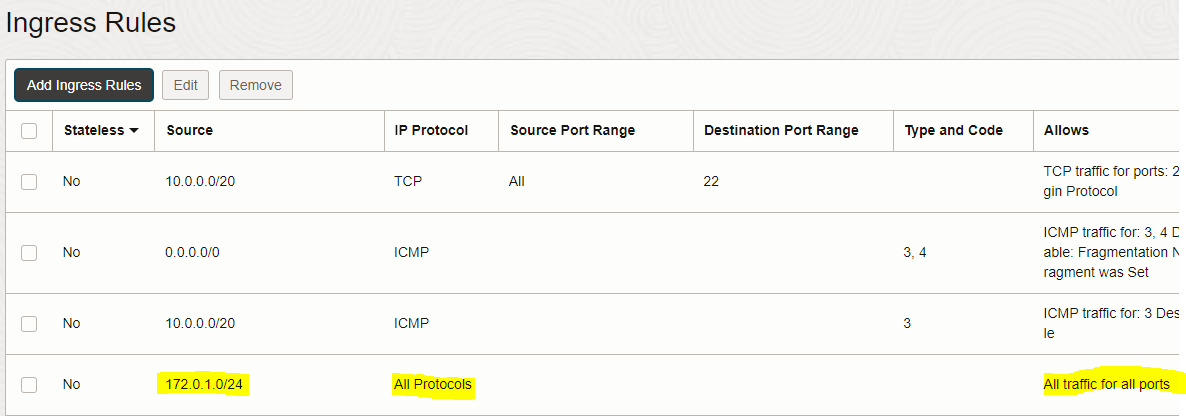
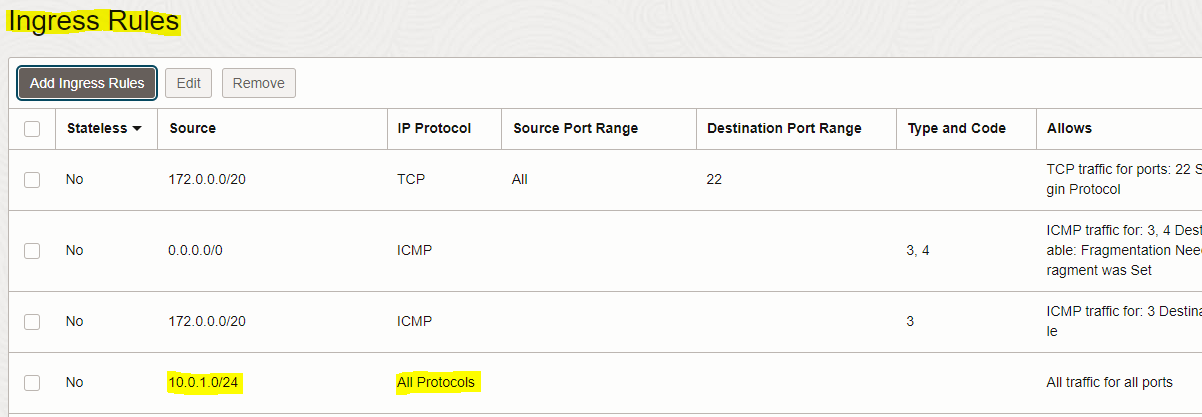
– Repeat the same steps done above to add the Ingress rule for VCN1, but use the below Ingress rule
|
Source Type |
Source CIDR |
IP PROTOCOL |
|
CIDR |
10.0.1.64/24 (VCN1-private subnet CIDR) |
All Protocols |
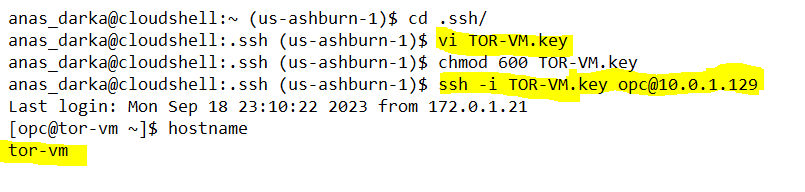
– Use RSA private key, which was generated while creating ASH-VM, to ssh from TOR-VM to opc@ASH-VM.
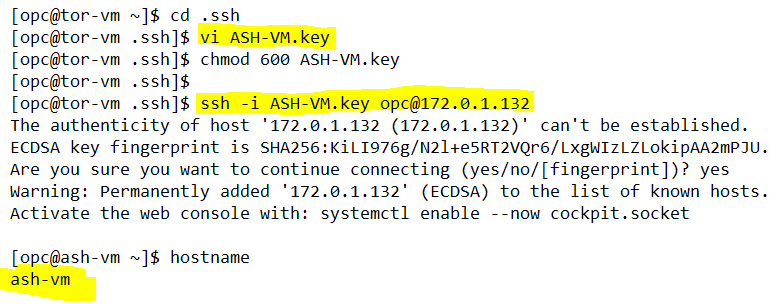
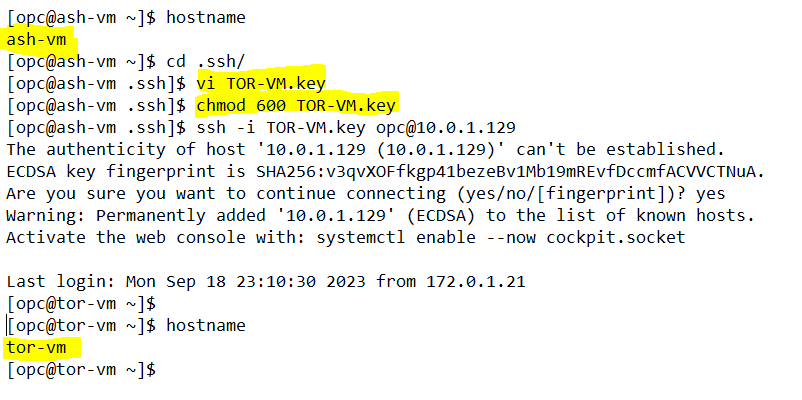
Thanks for reading!
Overview: Oracle 23c database introduces a new feature to open Pluggable database in a new mode called hybrid read-only Hybrid read-only mode enables ... Read More
Overview: A MySQL configuration is a collection of variables that define the operation of a MySQL DB system. It is analogous to ... Read More