Oracle 23c: Managing Flashback Database Logs Outside the Fast Recovery Area
Overview: In previous Database releases, you could store flashback database logs only in the fast recovery area Oracle 23c Database introduces the ... Read More
Learn more about why Eclipsys has been certified as a Great Place to Work in Canada, Best Workplaces in Ontario and Technology, and named Canada’s Top SME Employer for 3 years!
Learn more!Local VCN peering is the process of connecting two VCNs in the same region so that their resources can communicate using private IP addresses without routing the traffic over the internet or through your on-premises network. The VCNs can be in the same Oracle Cloud Infrastructure (OCI) tenancy or different ones.
A peering is a single peering relationship between two VCNs. Example: If VCN1 peers with three other VCNs, then there are three peerings.

In this blog, we will demonstrate the steps to set up a local peering between the private subnets of two VCNs in the same tenancy.
At a high level:
|
|
VCN1 |
VCN2 |
|
VCN Name |
TOR-VCN1 |
TOR-VCN2 |
|
Private Subnet CIDR |
172.10.0.64/26 |
172.20.0.64/26 |
|
LPG |
VCN1-LPG |
VCN2-LPG |
|
Compute Instance |
VCN1-VM (172.10.0.124) |
VCN2-VM (172.20.0.124) |
Prerequisites:
Restrictions:
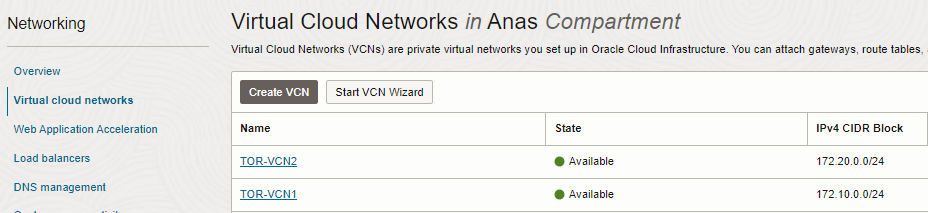
1. Create LPG (VCN1-LPG) for the first VCN (TOR-VCN1)


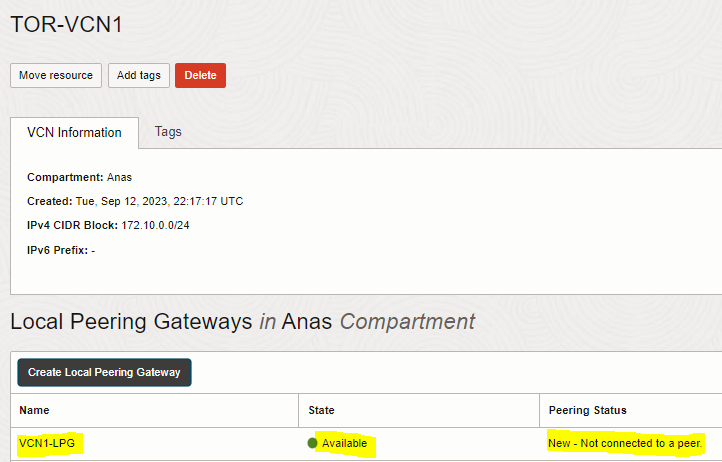
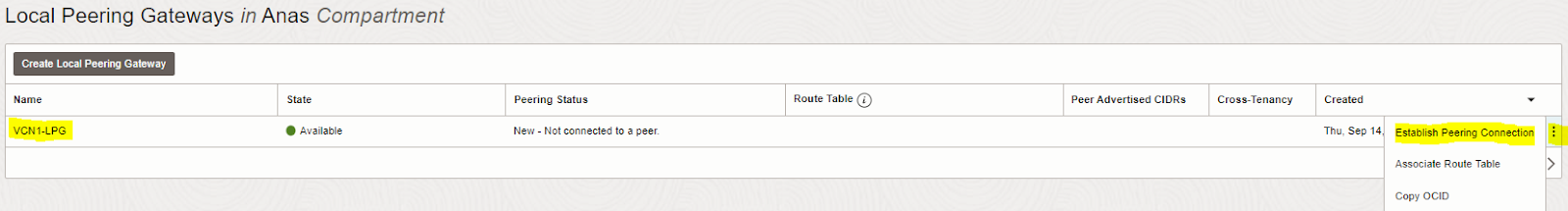
2. Create LPG (VCN2-LPG) for the second VCN (TOR-VCN2). Repeat the same steps done above to create VCN1-LPG



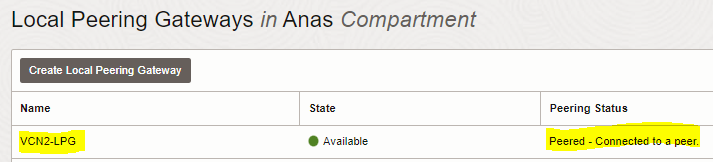
Hence, peering connection is done as well from VCN2-LPG to VCN1-LPG.
1. Add route rule to “route table for private subnet” of the first VCN (TOR-VCN1) to enable routing to the private subnet of the second VCN

|
Target Type |
Destination CIDR Block |
Target Local Peering Gateway |
|
Local Peering Gateway |
172.20.0.64/26 (VCN2-private subnet CIDR) |
VCN1-LPG |
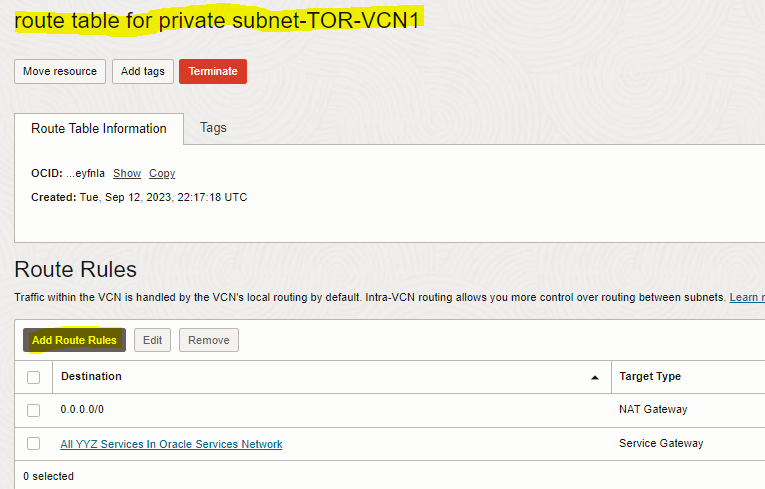
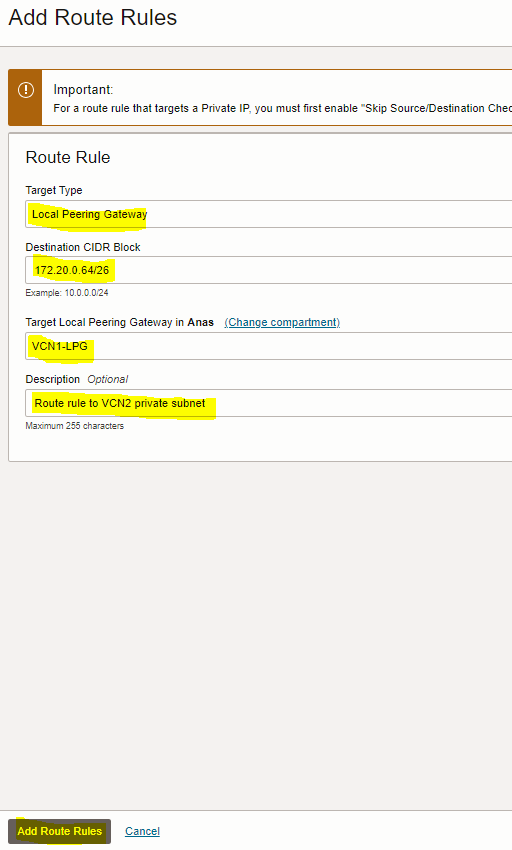
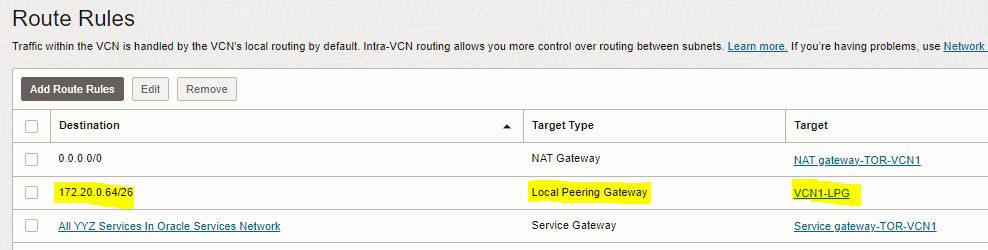
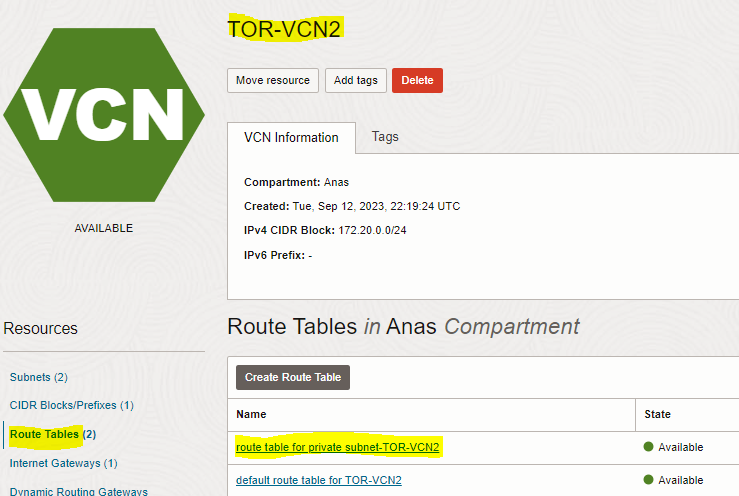
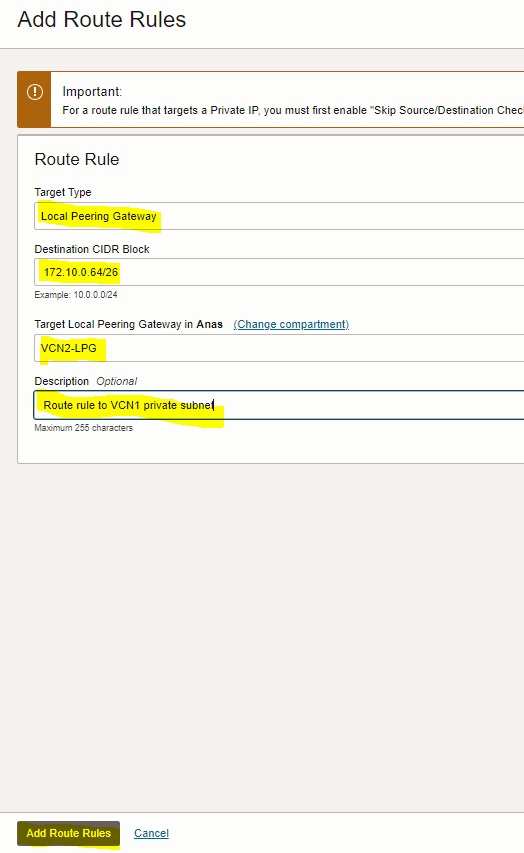
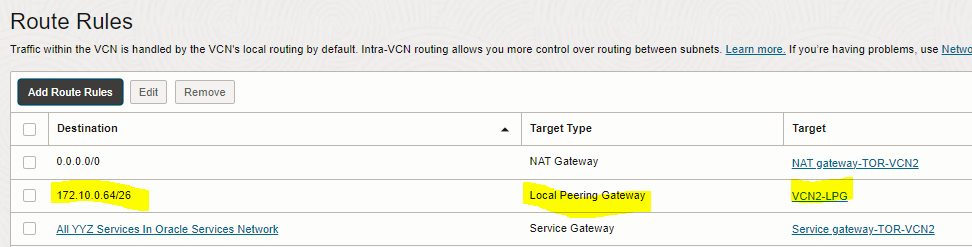
2. Add route rule to “route table for private subnet” of the second VCN (TOR-VCN2) to enable routing to the private subnet of the first VCN
|
Target Type |
Destination CIDR Block |
Target Local Peering Gateway |
|
Local Peering Gateway |
172.10.0.64/26 (VCN1-private subnet CIDR) |
VCN2-LPG |

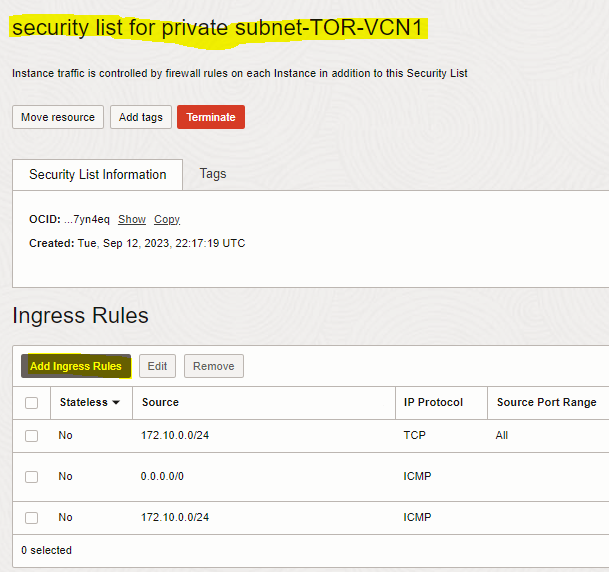
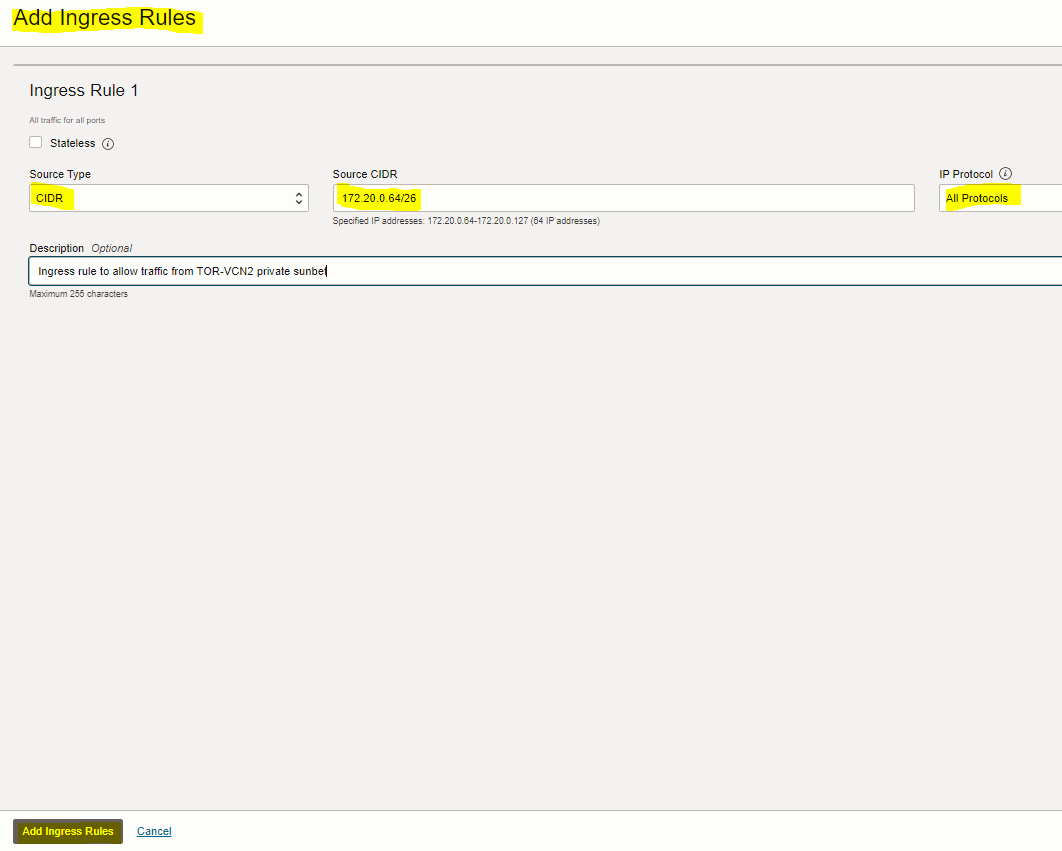
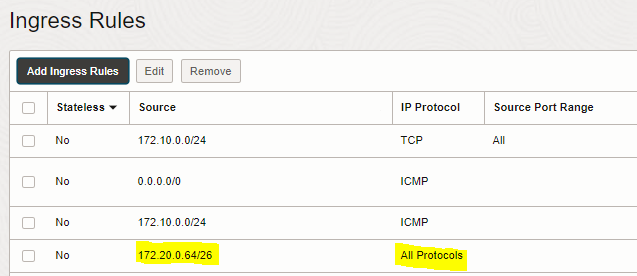
1. Add Ingress rule to “security list for private subnet-TOR-VCN1” of the first VCN (TOR-VCN1) to allow traffic coming from VCN2-private subnet to VCN1-private subnet

|
Source Type |
Source CIDR |
IP PROTOCOL |
|
CIDR |
172.20.0.64/26 (VCN2-private subnet CIDR) |
All Protocols |
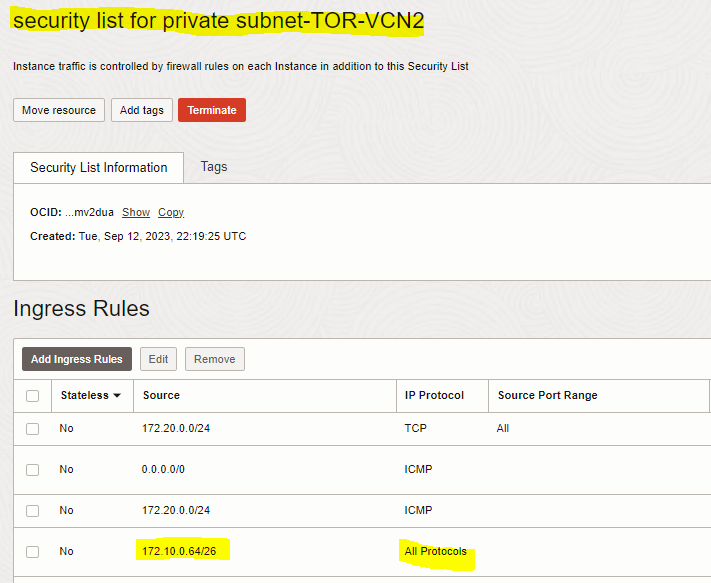
2. Add Ingress rule to the “security list for private subnet-TOR-VCN2” of the first VCN (TOR-VCN2) to allow traffic coming from VCN1-private subnet to VCN2-private subnet
|
Source Type |
Source CIDR |
IP PROTOCOL |
|
CIDR |
172.10.0.64/26 (VCN1-private subnet CIDR) |
All Protocols |
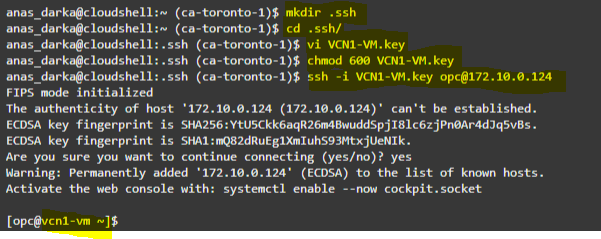
1. Connect to VCN1-VM, then ssh to VCN2-VM
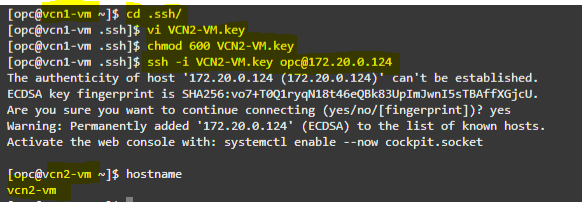
2. Connect to VCN1-VM, then ssh to VCN2-VM. Repeat the same steps

Thanks for reading!
Overview: In previous Database releases, you could store flashback database logs only in the fast recovery area Oracle 23c Database introduces the ... Read More
Overview: Oracle 23c Database introduces a new feature to control whether a user or session is enabled for read-write operations, irrespective of the ... Read More