Oracle 23c: Managing Flashback Database Logs Outside the Fast Recovery Area
Overview: In previous Database releases, you could store flashback database logs only in the fast recovery area Oracle 23c Database introduces the ... Read More
Apprenez-en plus sur les raisons pour lesquelles Eclipsys a été certifié comme un excellent lieu de travail au Canada, les meilleurs lieux de travail en Ontario et en technologie, et a été nommé le meilleur employeur de PME au Canada pendant 3 ans !
En savoir plus !We have started the workshop in the previous blog “Oracle OCI Site-to-Site VPN to Meraki Switch – Part 2” where we covered the steps to create DRG, a private subnet, and a security list.
In this blog, we will complete the workshop by creating a Site-to-Site VPN configuration and then configuring the Meraki Cisco switch.
We will use the wizard to set up a Site-to-Site VPN. The wizard sets up a Site-to-Site VPN between your on-premises network and your Oracle VCN. That includes the IPSec encrypted tunnels and customer-premises equipment (CPE).
1. Open the navigation menu, click “Networking”, and then click “Site-to-Site VPN”
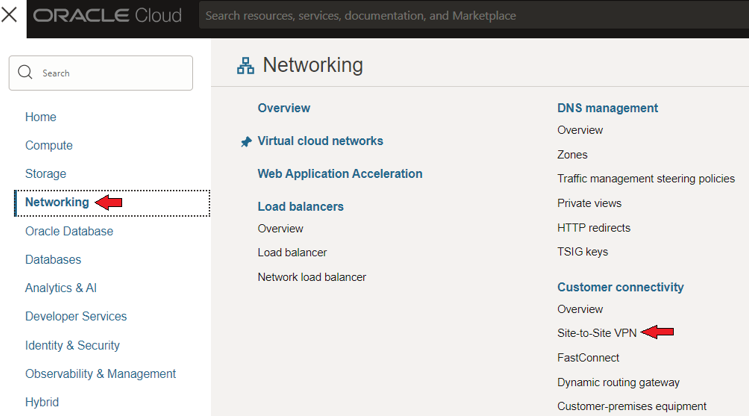
2. Click “Start VPN wizard”.
3. In the “Create Site-to-Site VPN” dialog window, in the “Basic information” window select VCN’s compartment and VCN name, then click next. DRG and IGW will be automatically populated.

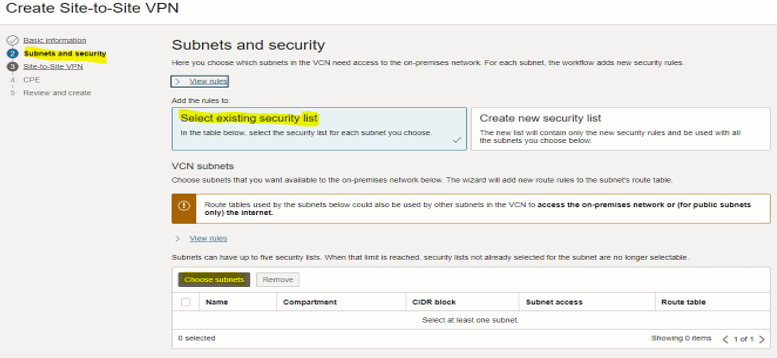
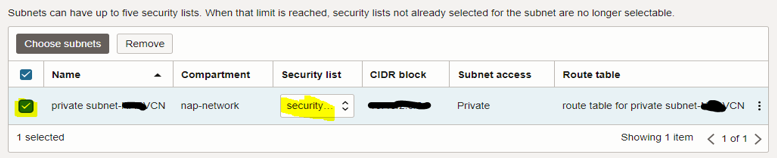
In the “Subnets and security” window, select the “Select existing security list” option, and click “Choose subnets” to select a private subnet.
In the “Choose subnets” dialog window, select private subnet, and click “Choose subnets”

Make sure to select the correct Security list created in step #4 from the previous blog.
In the “Site-to-Site VPN” window, enter and select the below options then click “Next”

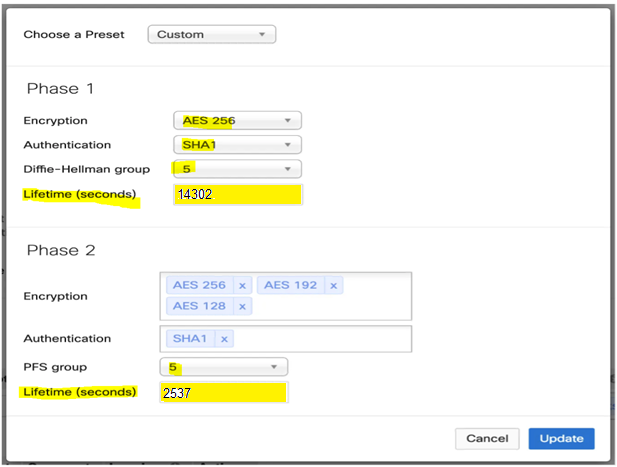
In the “Tunnel 1 & 2 information” section select the below options
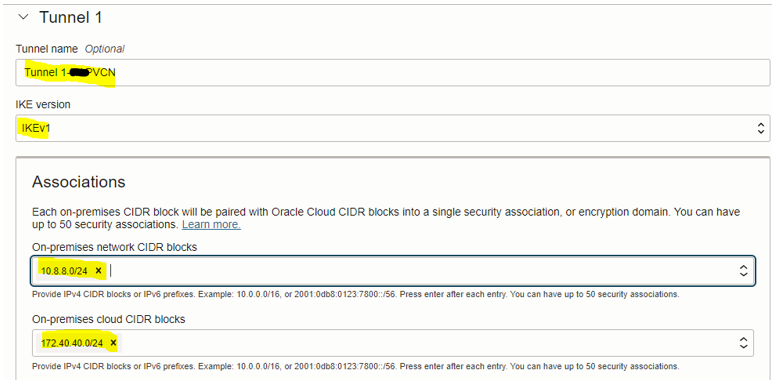
In the “CPE” window, enter and select the below information, and click “Next”

In the “Review and Create” window, click “Create VPN solution” at the bottom. Once provisioning completes VPN state will be available.
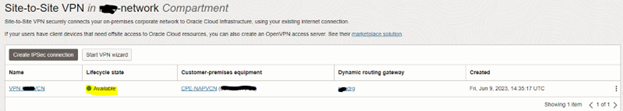
4. Click the VPN name to collect tunnel information. The below information is required to configure the on-premises Meraki switch.
Note: You will notice that there are two IPSec Tunnels from Oracle’s side. Meraki only supports connecting to one at a time.
– Tunnel 1 public IP address – Oracle VPN IP address
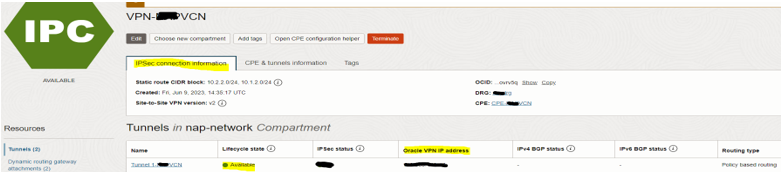
– Tunnel 1 shared secret
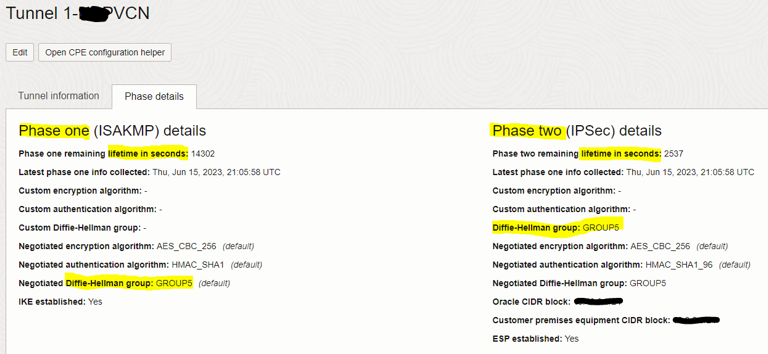
– Phase details: click on Tunnel 1 name then navigate to the “Phase details” tab. Required information
Note: You will notice that there are two IPSec Tunnels from Oracle’s side. Meraki only supports connecting to one at a time.
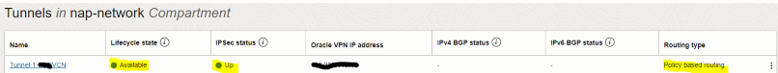
Once the Meraki switch configuration is completed Oracle tunnel status will be up
We’re all done provisioning, and you should now be able to ping and SSH from on-premises to the Oracle compute instance located in the private subnet.
You can access VPN logs as shown below.
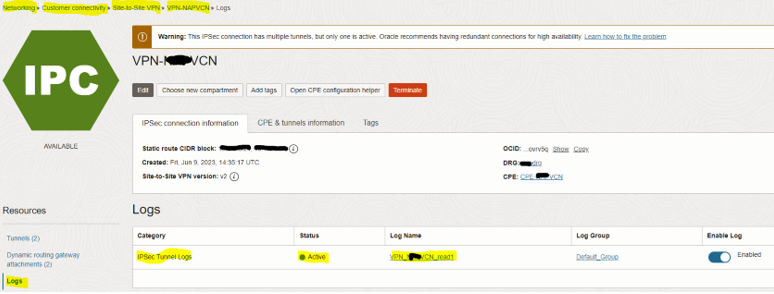
The workshop is completed. IPSec VPN connection between your on-premises and Oracle VCN private subnet is ready now!
Overview: In previous Database releases, you could store flashback database logs only in the fast recovery area Oracle 23c Database introduces the ... Read More
Overview: Oracle 23c Database introduces a new feature to control whether a user or session is enabled for read-write operations, irrespective of the ... Read More