OLVM: Upgrade from 4.4 to 4.5
Introduction VMware vSphere has long held the crown as the leading on-premises server virtualization solution across businesses of all sizes. Its ... Read More
Découvrez pourquoi Eclipsys a été nommée 2023 Best Workplaces in Technology, Great Place to Work® Canada et Canada's Top 100 SME !
En savoir plus !
We live in a digital era where the most valuable asset is data. Most organizations are investing in the cloud to take a business edge to become more competitive in the market. When their databases are migrated to the cloud next stride is taken to protect the data. But not having a proper monitoring dashboard and understanding of data may lead to sudden data breaches. Without understanding what kind of data you have it’s impossible to drill down to implement data protection elements like data masking.
A protection method must be implemented on all environments like Dev, Test, Pre-Prod, and UAT. Databases are the key component in any organization. During the Audit time period security administrators spend hours gathering information related to the database security measurements. But having a centralized dashboard to view all the activity help to understand the data and implement proactive measurements to protect data. Oracle data safe is a powerful and flexible tool to protect Oracle databases. Data-Safe is a unified control center for managing database security in the Oracle Cloud, both for your Oracle Cloud Databases and your Oracle On-Premises Databases.
To protect your enterprise data, you need to be able to answer a number of questions such as:
Data Safe allows customers to perform security and user assessments of their database and their database users
Data Safe manages database server audit policies and securely collects, removes, and retains audit data from database servers
Data Safe discovers sensitive data in databases:
Data Safe masks sensitive data in development and test databases:
Data Safe dashboard allows customers to quickly assess and then drill down to review risk:
Also, this can be met to be compliant with:
In this article, I will illustrate how can to discover the data from data-safe.
If you are still new to data safe, refer to Data Safe.
First, navigate the dashboard and select data discovery
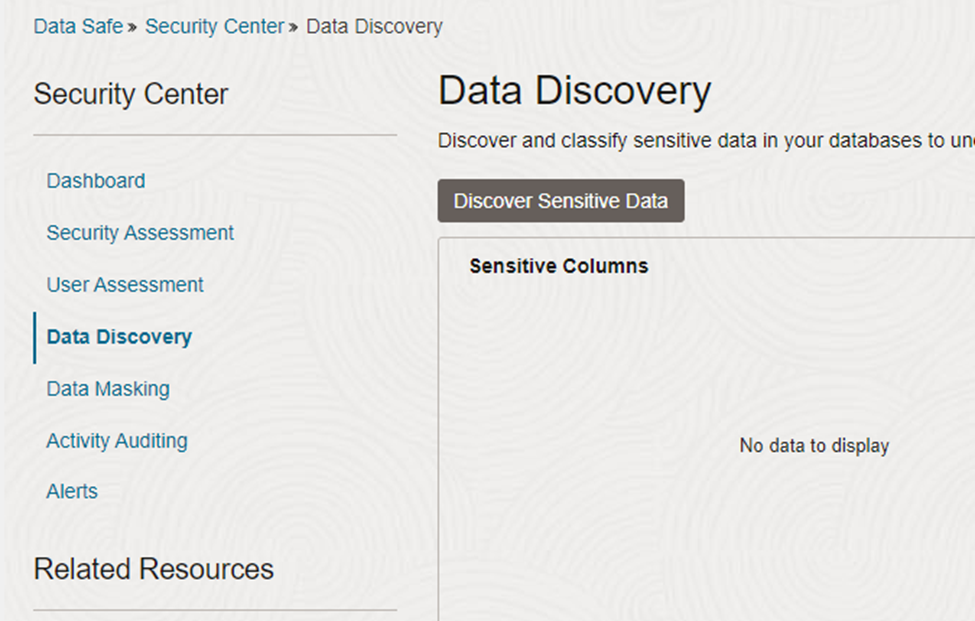
Figure 1: Select data discovery
This window discovers the schemas and you can select the respective schema.
As per this example select Scott schema.
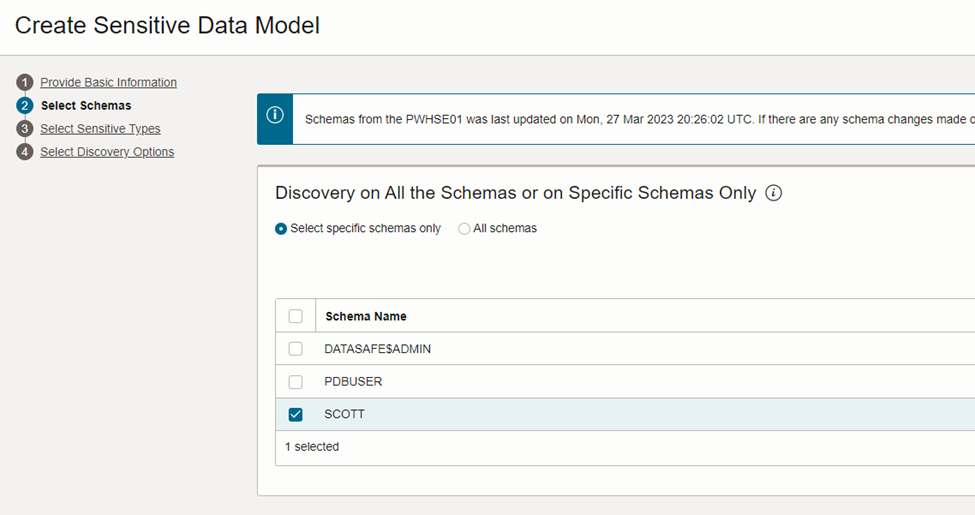
Figure 2: Select the schema
Below mentioned window enables you to select the type of data there in the schema.
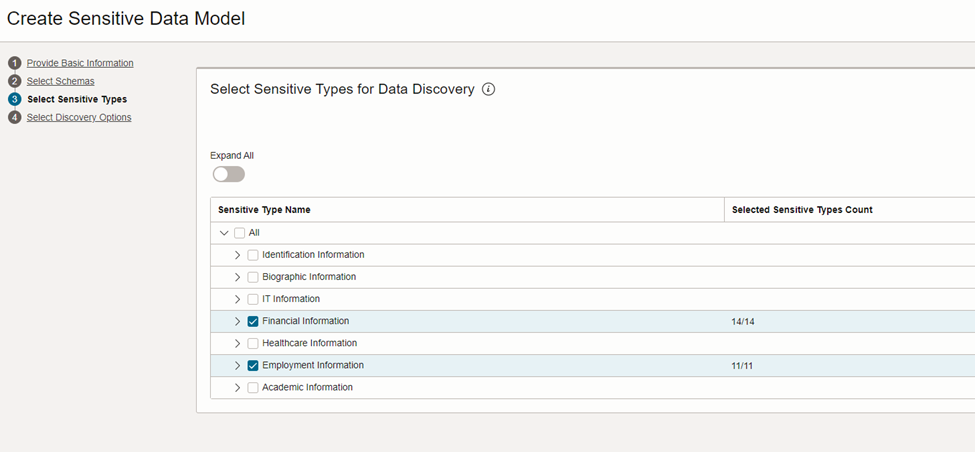
Figure 3: Selecting data type.
As per Figure 4: you can tic the discovery option to collect the data and discover the data with referential relationships.
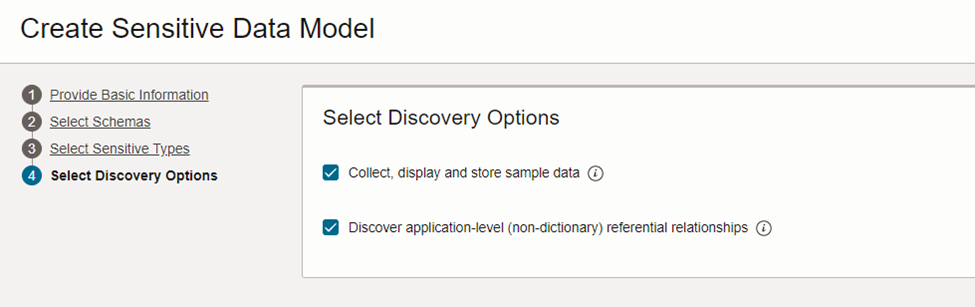
Figure 4: Sensitive data model.
Oracle has to introduce discover and classify sensitive data based on a library of more than 150 predefined sensitive data types that easily can be broadened with customer data types to meet any organization’s requirement. This helps to classify the amount of sensitive data within databases and use that information to determine associated risks and data protection needs.
Some of the predefined data examples
Figure 5 pie chart illustrates the classification of data after the discovery
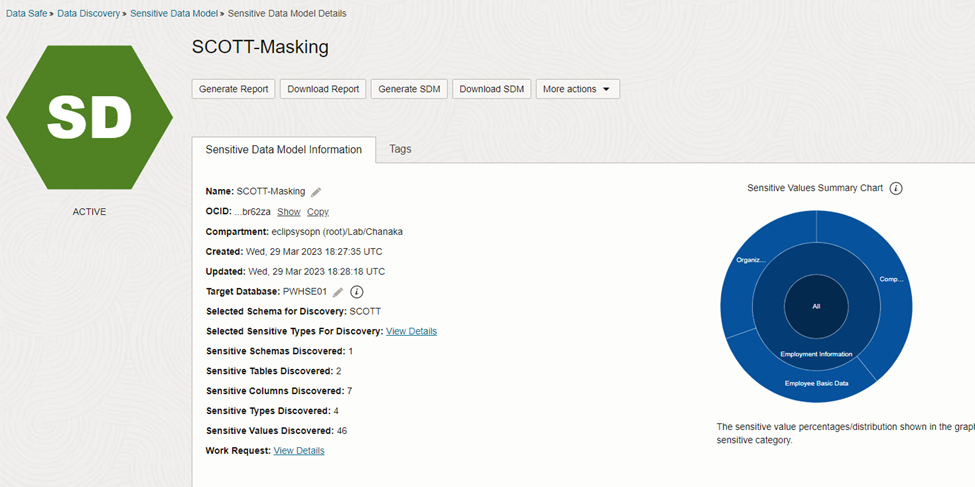
Figure 5: Data category pie chart.
Also this oracle data safe help us to understand the type of data from a column and what is the sensitive type of that classification. Figure 6 elaborates on columns with sensitive type.
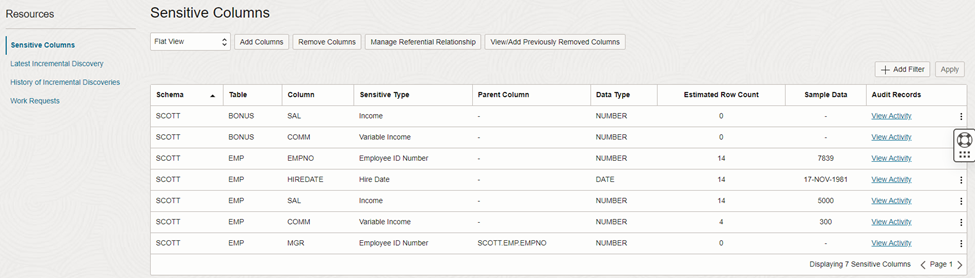
Figure 6: Discover schema columns.
The next step is data masking, I will discuss these steps in my next article.
Data is the new currency. It is one of the most valuable organizational assets, however, if that data is not well protected, it can quickly become a liability. At an alarming rate we are seeing more and more data breaches that impact an organization’s brand, their ability to continue to deliver services and do business, and of course, they are impacted financially. The only possible way to overcome this is by having a proper data security monitoring tool.
Oracle Data Safe in OCI really powerful tool that elevates database security. This tool helps to understand the amount of sensitive data stored in the database. Oracle predefined library help to classify sensitive data and determine the associated risk and data protection needs. Even data safe reduces the data risk of the database and eliminate these associated risk by implementing masking these risk by feature.
About me :

Introduction VMware vSphere has long held the crown as the leading on-premises server virtualization solution across businesses of all sizes. Its ... Read More
Introduction Monitoring plays a major part in mission-critical environments. Most businesses depend on IT infrastructure. As the ... Read More