OCI FortiGate HA Cluster – Reference Architecture: Code Review and Fixes
Introduction OCI Quick Start repositories on GitHub are collections of Terraform scripts and configurations provided by Oracle. These repositories ... Read More
Découvrez pourquoi Eclipsys a été nommée 2023 Best Workplaces in Technology, Great Place to Work® Canada et Canada's Top 100 SME !
En savoir plus !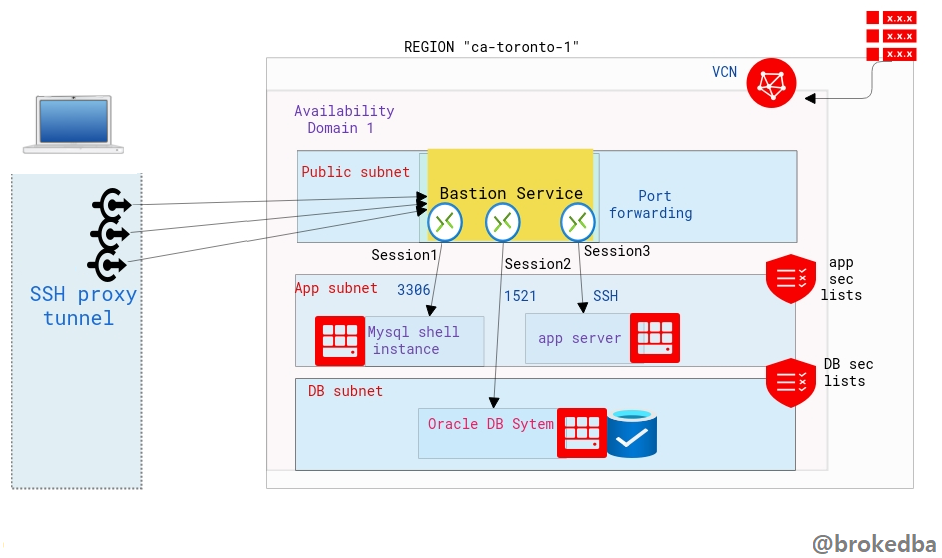
In the Cloud, Bastion or Jump Server is the only node exposed to the outside world and acts as a gateway between the Private Network where your backend resources (application, databases and other applications) are hosted and the Internet. A Bastion runs bare minimum applications and is extremely secure. Even if any network can access it, it is still fortified against illegal entry and attack.
But What if there was another disruptive way to provide that sort of remote access without needing to configure a VM (Virtual Machine) in a Public Subnet?
A quick table of contents
– What is Bastion Service and Why is it, Revolutionary
– Create Bastion Service using the Console
Let me demonstrate why OCI Bastion (Oracle Cloud Infrastructure) service makes your life easier. Imagine every team in your organization wanting their own Bastion VM because hey they’re no fan of sharing their stuff with others. For each of your teams you would have to:
– Create a Public Subnet
– Create a VM in that Subnet
– Ensure the hardening and constant auditing of your bastion VMs
– Pay for the CPU and other resources of your bastion VM for each team
OCI Bastion Service is a FREE serverless, clientless connectivity that enables you to connect from anywhere on any device or platform-(without an additional agent installation) to your instances In your Private Subnets.
You can leverage the ssh tunnel for literally any port via the port-forwarding feature. Your target system can be a database compute instance (DBCS, MYSQL, EXACS etc.) or any app server within your Private Subnets.
Why OCI Bastion Service is better than other provider’s equivalent offerings
Exactly, with the Oracle Bastion service, you not only won’t need to worry about creating, hardening or paying for a bastion VM anymore, but the service is FREE and you won’t have to install any agent or grant permissions.
Let’s see how to create the bastion service through the Console, OCI CLI, and terraform. The bastion service is linked to the target subnet and a bastion session will define the port forwarding to the target instance.
Our environment :
– VCN vcnterra has the private subnet db-sub with a CIDR of 192.168.78.0/24
– DB instance IP is 192.168.78.10

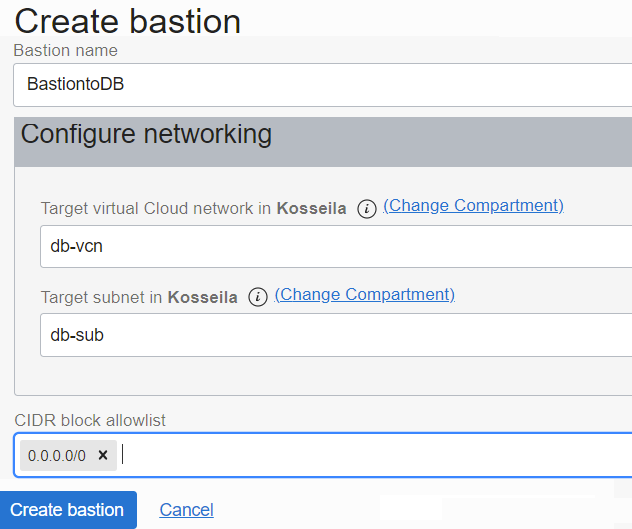
CIDR allowlist: 0.0.0.0/0 means you can SSH the DB instance from anywhere.
We will now create the Bastion session where we will define the forwarded port through the tunnel and the target IP
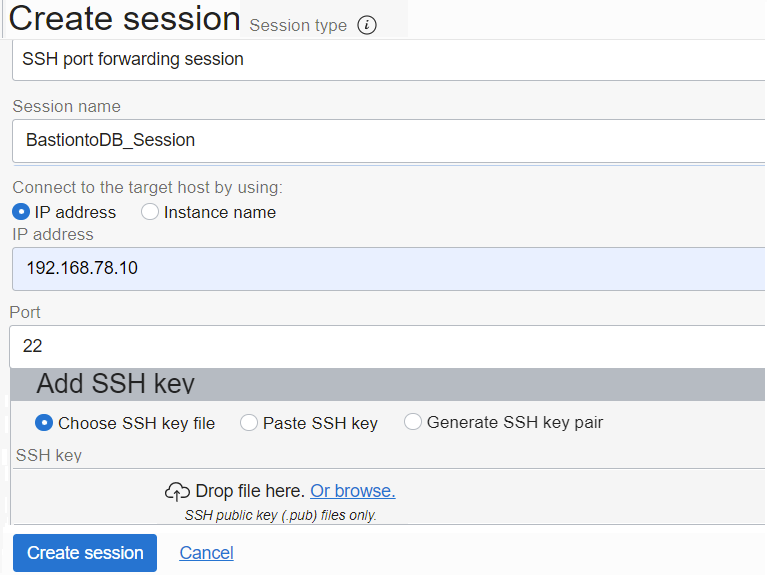
Note:
There are two session types, SSH Managed which requires a cloud agent and port forwarding session which we need.
You can either generate, upload, or paste your SSH public key.
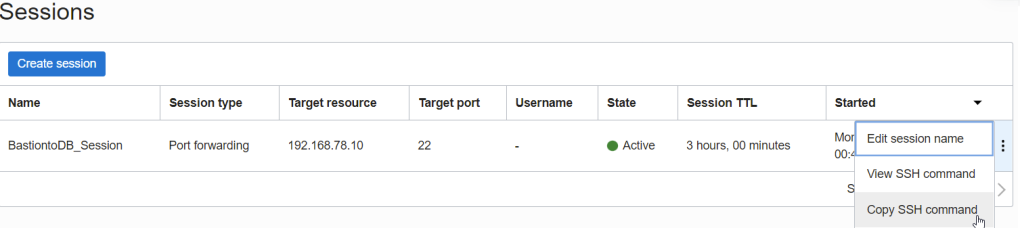
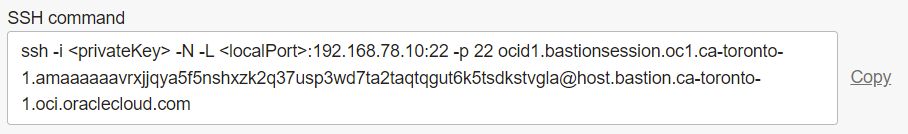
# ssh -i ~/.ssh/id_rsa_oci -N -L 22:192.168.78.10:22 -p 22 ocid1.bastionsession.oc1.ca-toronto-1.amaaaaaavr**a@host.bastion.ca-toronto-1.oci.oraclecloud.com &
# ssh -i ~/.ssh/id_rsa_dbcs opc@localhost
[opc@hopsdb-oci ~]$ cat /etc/redhat-release --- target instance
Red Hat Enterprise Linux Server release 7.9 (Maipo)
[opc@hopsdb-oci ~]$ ifconfig ens3
ens3: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 9000
inet 192.168.78.10 netmask 255.255.255.0 broadcast 192.168.78.255
In this article, we learned
Introduction OCI Quick Start repositories on GitHub are collections of Terraform scripts and configurations provided by Oracle. These repositories ... Read More
Introduction So far, I have used Oracle AutoUpgrade, many times in 3 different OS’. Yet the more you think you’ve seen it all and reached the ... Read More